0x01 题目
附件是一个apk包
0x02 解题
解压apk包之后发现被加密了,用apktools进行解密,然后反编译得到源码:
找到入口类,在com.example.haveaandroid:
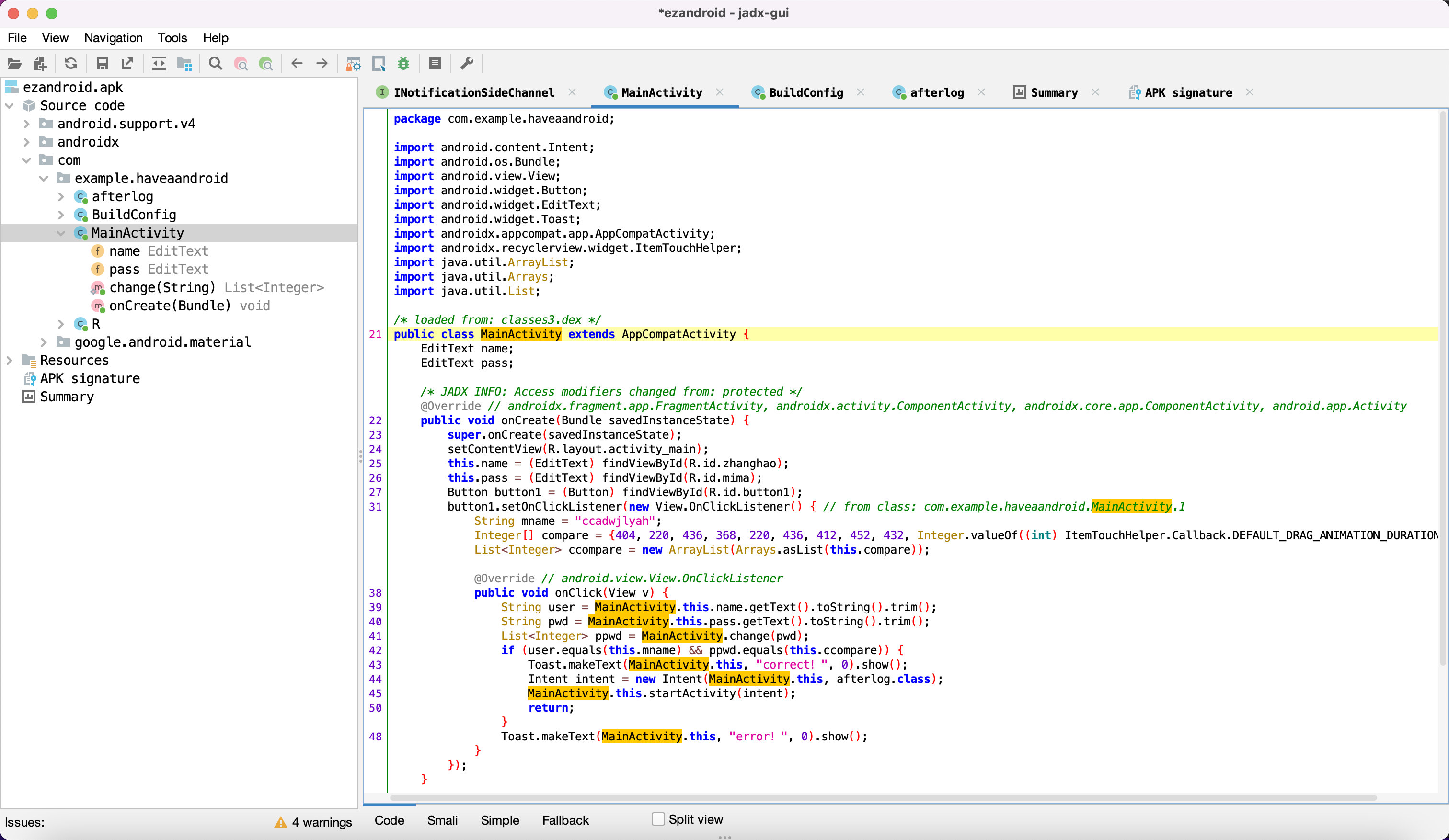
源码如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
| package com.example.haveaandroid;
import android.content.Intent;
import android.os.Bundle;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import androidx.recyclerview.widget.ItemTouchHelper;
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
public class MainActivity extends AppCompatActivity {
EditText name;
EditText pass;
@Override
public void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
this.name = (EditText) findViewById(R.id.zhanghao);
this.pass = (EditText) findViewById(R.id.mima);
Button button1 = (Button) findViewById(R.id.button1);
button1.setOnClickListener(new View.OnClickListener() {
String mname = "ccadwjlyah";
Integer[] compare = {404, 220, 436, 368, 220, 436, 412, 452, 432, Integer.valueOf((int) ItemTouchHelper.Callback.DEFAULT_DRAG_ANIMATION_DURATION), 412};
List<Integer> ccompare = new ArrayList(Arrays.asList(this.compare));
@Override
public void onClick(View v) {
String user = MainActivity.this.name.getText().toString().trim();
String pwd = MainActivity.this.pass.getText().toString().trim();
List<Integer> ppwd = MainActivity.change(pwd);
if (user.equals(this.mname) && ppwd.equals(this.ccompare)) {
Toast.makeText(MainActivity.this, "correct!", 0).show();
Intent intent = new Intent(MainActivity.this, afterlog.class);
MainActivity.this.startActivity(intent);
return;
}
Toast.makeText(MainActivity.this, "error!", 0).show();
}
});
}
public static List<Integer> change(String args) {
List<Integer> list = new ArrayList<>();
char[] ch = args.toCharArray();
for (char c : ch) {
int xxx = (c ^ 3) << 2;
list.add(Integer.valueOf(xxx));
}
return list;
}
}
|
可以直接看到打开app之后需要输入登入用户名和密码,其中用户名已经给出:
1
| String mname = "ccadwjlyah";
|
而密码则通过change函数进行异或和移位进行加密,加密前的密文为:
1
| Integer[] compare = {404, 220, 436, 368, 220, 436, 412, 452, 432, Integer.valueOf((int) ItemTouchHelper.Callback.DEFAULT_DRAG_ANIMATION_DURATION), 412};
|
这里面的Integer.valueOf((int) ItemTouchHelper.Callback.DEFAULT_DRAG_ANIMATION_DURATION)是一个常量,通过逆向追踪找到了它的数值:
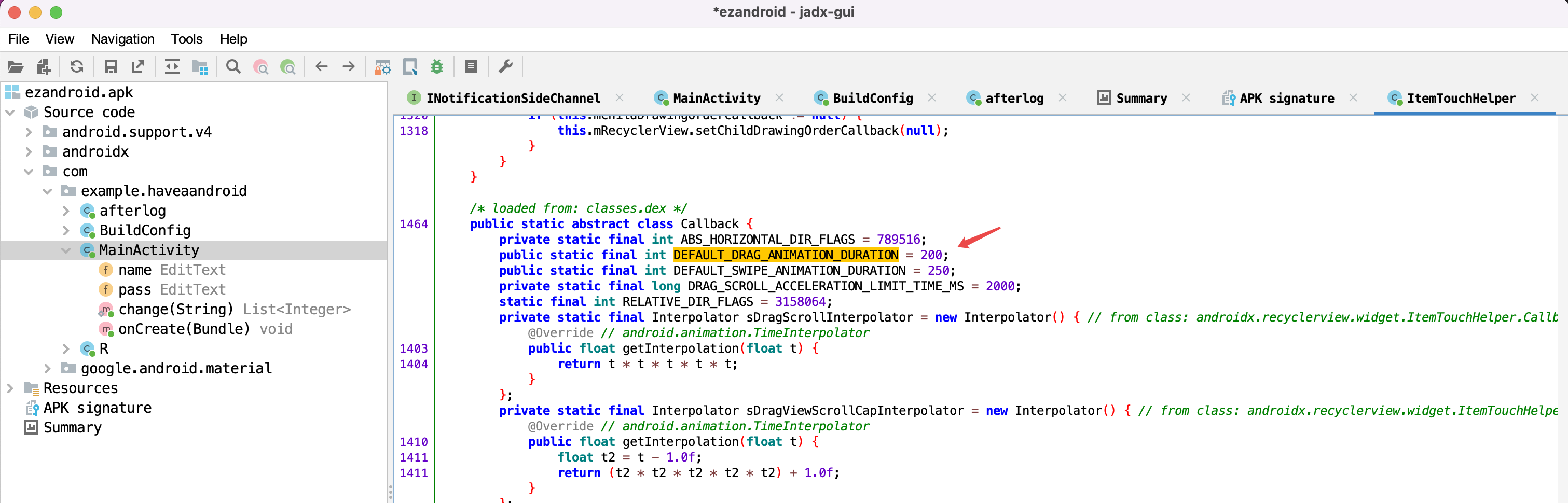
将Integer.valueOf((int) ItemTouchHelper.Callback.DEFAULT_DRAG_ANIMATION_DURATION)替换成它的数值,得到了我们寻找的密码密文:
1
| Integer[] compare = {404, 220, 436, 368, 220, 436, 412, 452, 432, 200, 412};
|
根据public static List<Integer> change(String args)写出解密脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| package cn.q1jun;
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
public class main {
public static void main(String[] args) throws Exception {
Integer[] compare = {404, 220, 436, 368, 220, 436, 412, 452, 432, 200, 412};
List<Integer> ccompare = new ArrayList(Arrays.asList(compare));
for (int i: ccompare)
System.out.print(Character.toChars((i>>2)^3));
}
}
|
得到密码:
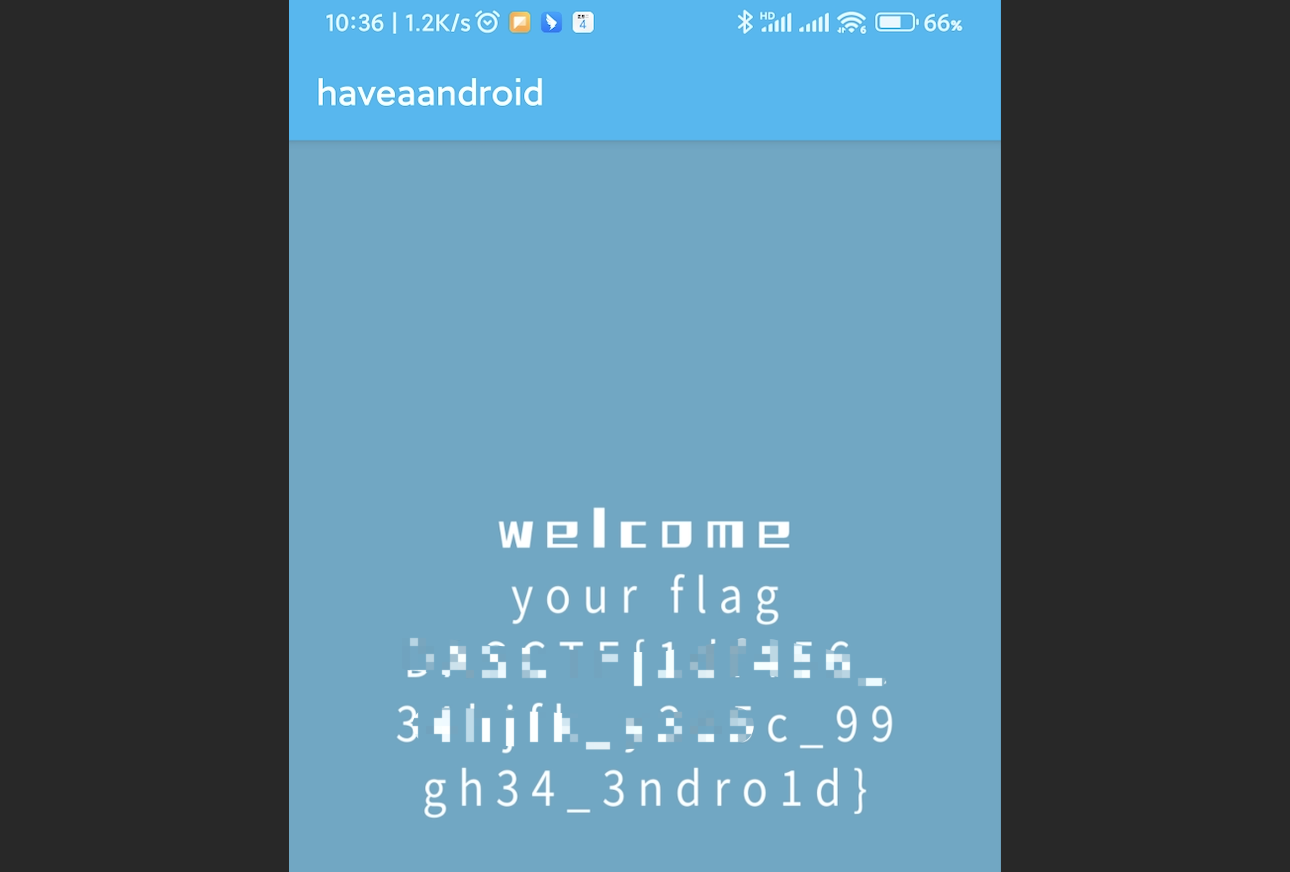
把apk安装一下,打开输入刚刚得到的用户名和密码:
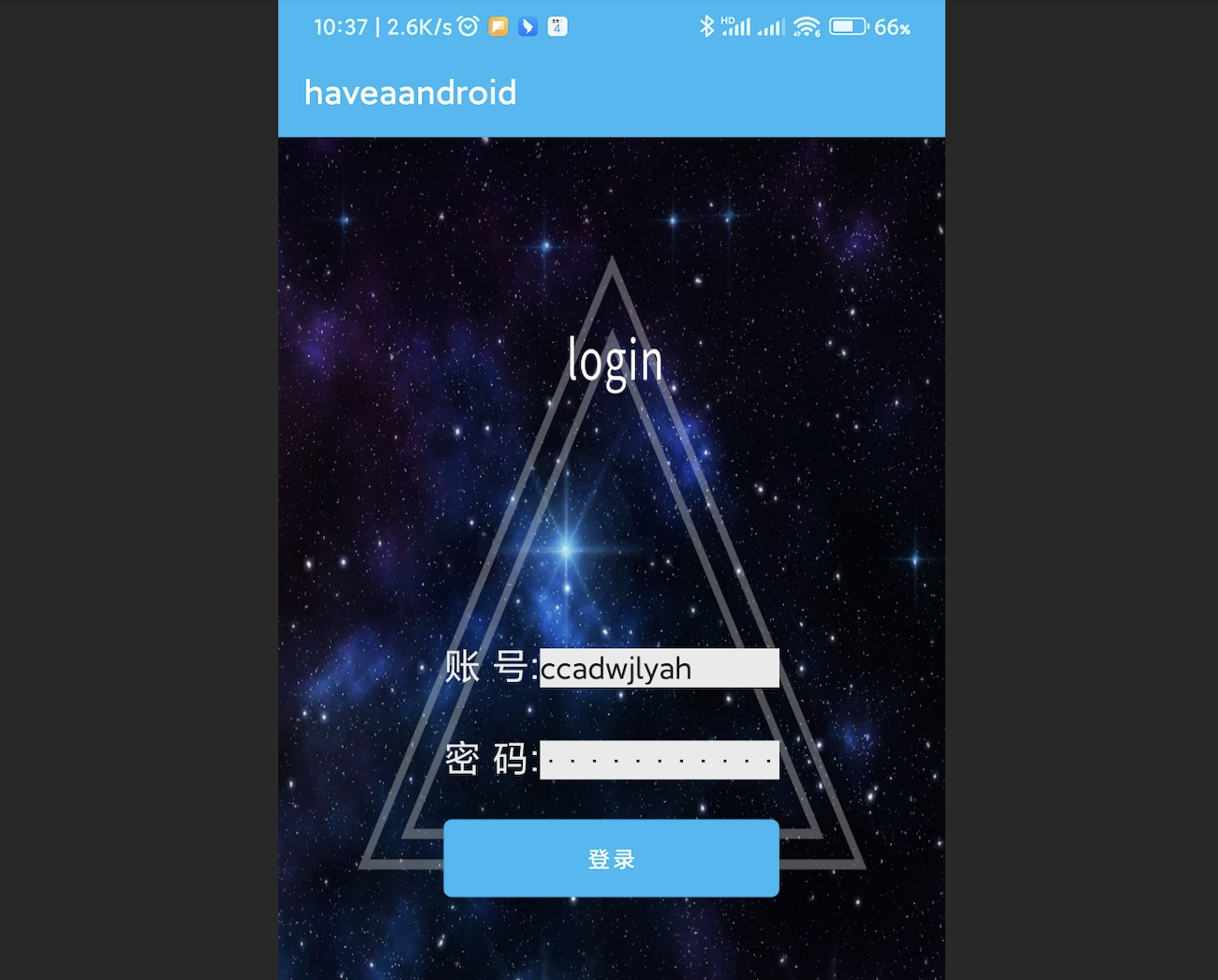
点击登入,即可获得flag: